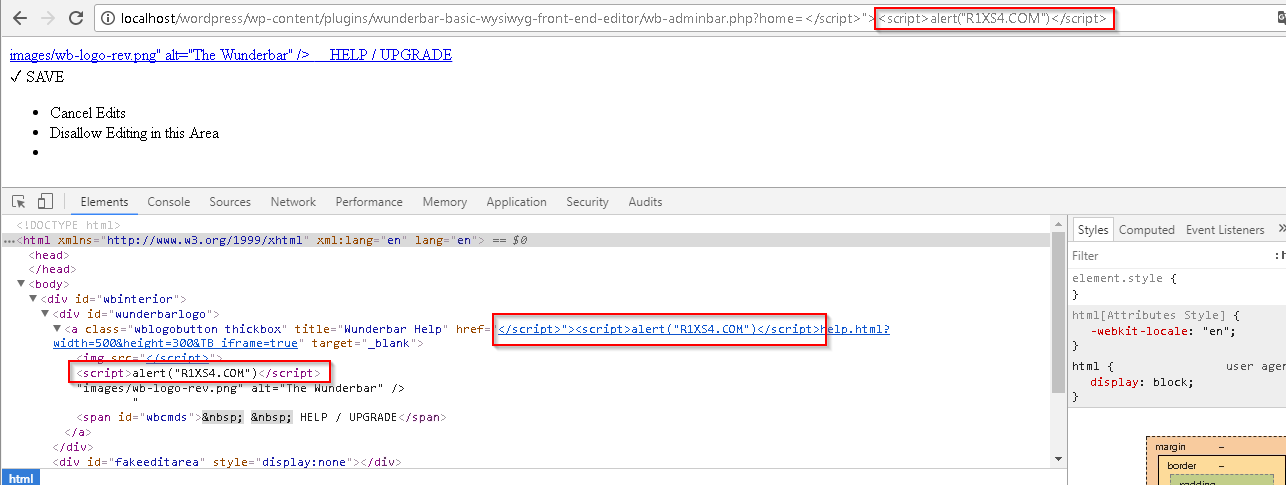
I continue found XSS into WordPress plugins, in this case the plugin is called “Wunderbar Basic” version 1.1.3.
The security bug is found in the “home” parameter in the”wp-content/plugins/wunderbar-basic-wysiwyyg-front-end-editor/wb-adminbar. php” file which, as can be seen in the following capture, lacks the necessary mechanisms to prevent code injection.
<div id="wbinterior" >
<div id="wunderbarlogo" >
<a class='wblogobutton thickbox' title='Wunderbar Help' href='<?php echo $_REQUEST['home']?>help.html?width=500&height=300&TB_iframe=true' target='_blank'>
<img src="<?php echo $_REQUEST['home']?>images/wb-logo-rev.png" alt="The Wunderbar" />
<span id='wbcmds'> HELP / UPGRADE</span>
</a>
</div>
<div id="fakeeditarea" style='display:none'></div>
The malicious code runs without problems.

This screenshot shows the code inside the HTML body.
- Publication in Packetstormsecurity:
https://packetstormsecurity.com/files/145434/WordPress-Wunderbar-Basic-1.1.3-Cross-Site-Scripting.html