In this post I show you how I found a Cross Site Scripting (XSS) Reflected in one of the subdomains of “General Motors”.

The first thing to make clear is that a company that is affiliated to a BugBounty program (hackerone.com) is allowed to analyze it. Remember that if they are not affiliated to these programs and we attack them, we can get into trouble, and we must warn them before publishing these vulnerabilities.
Another thing is that belonging to these programs means that the chances of finding some type of vulnerability are very low.
For this reason, it is advisable to search within their subdomains to increase the chances of finding any of the vulnerabilities in the OWASP Top 10:
In this case, I used the Sublist3r script (https://github.com/aboul3la/Sublist3r) to list the gm.com subdomains.
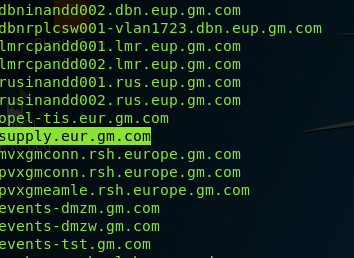
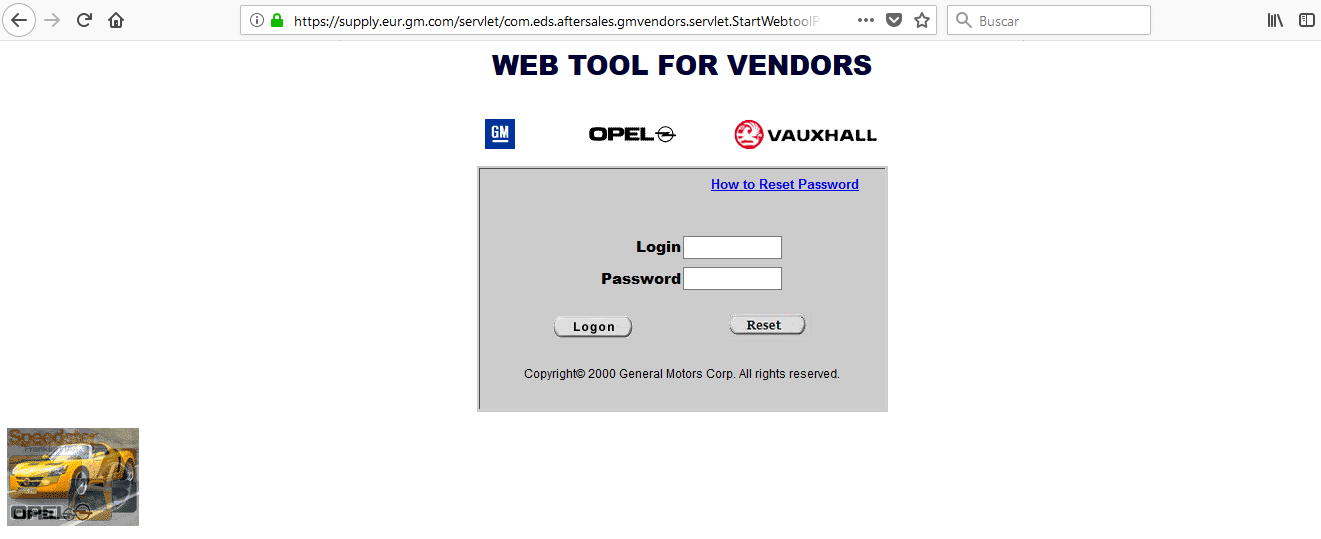
After weeks of searching, I will focus on the subdomain supply.eur.gm.com.
This subdomain caught my attention because it looks like an old website.
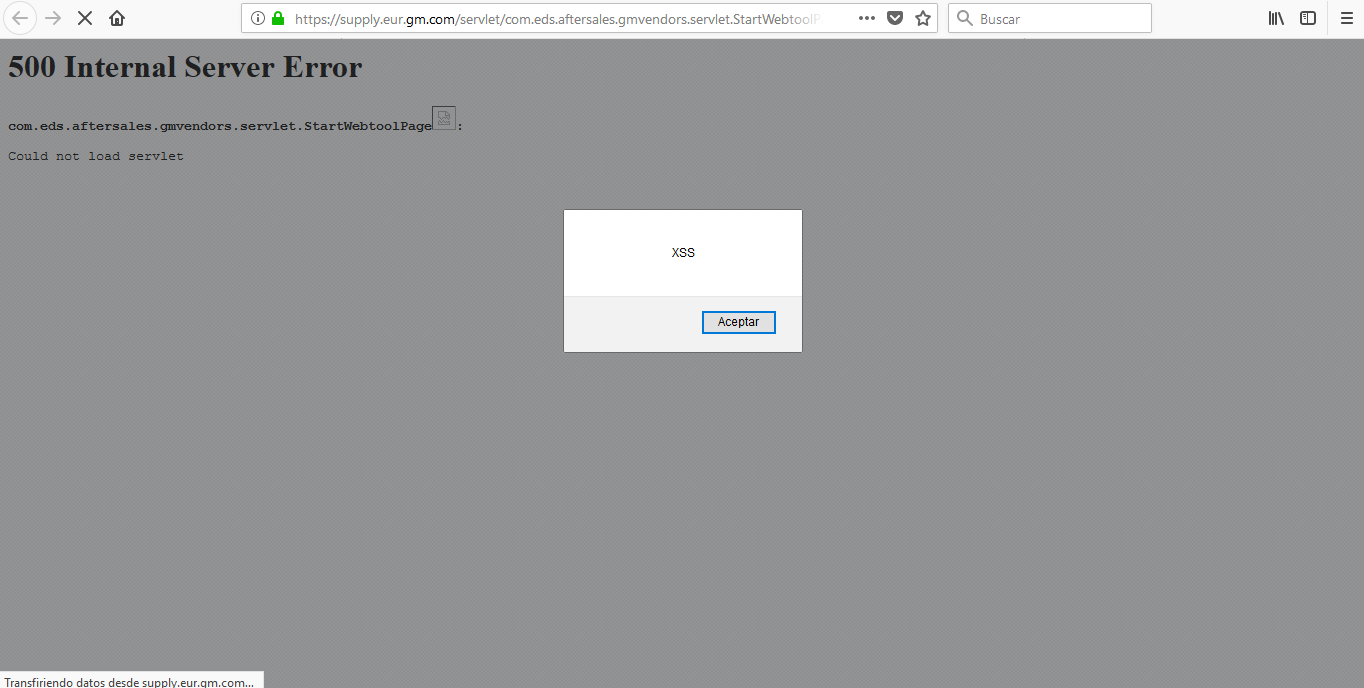
After making a lot of tests (users enumeration, directories listing, SQLi…) I found that it did not make a correct control of exceptions when forcing an error, moreover, this error showed me all the text contained in the URL.
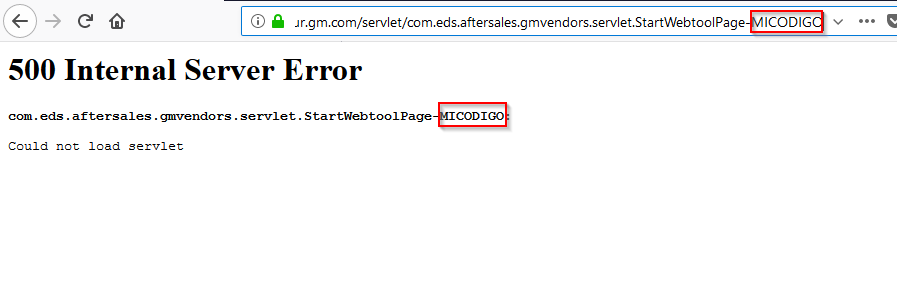
Taking advantage of this error, I generated an injection of JavaScript code by not correctly filtering the values entered in the URL.
Finally, I prepared two proofs of concept to send to the BugBounty program that GM has on the web https://www.hackerone.com/
[POC 1] Payload: <img%20src=a%20onerror=alert(“XSS”)>
[POC 2] Payload: <img onerror=javascript:window.location.replace(‘http:www.google.com’) src=”x”>
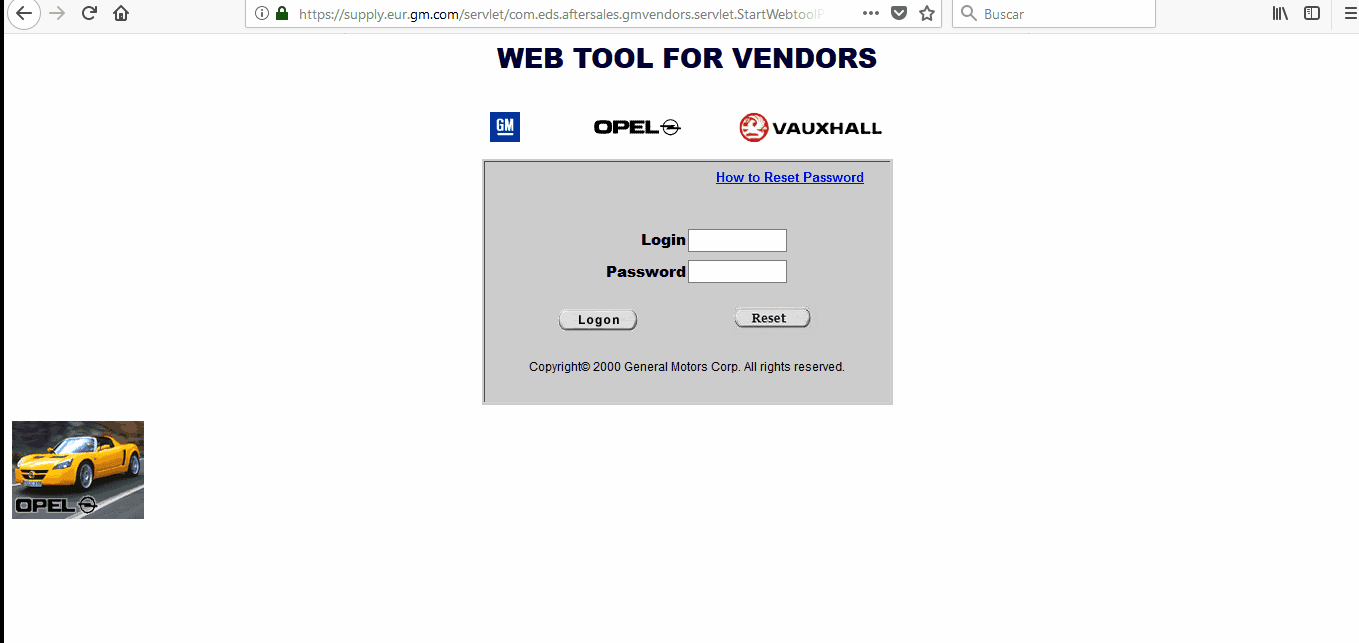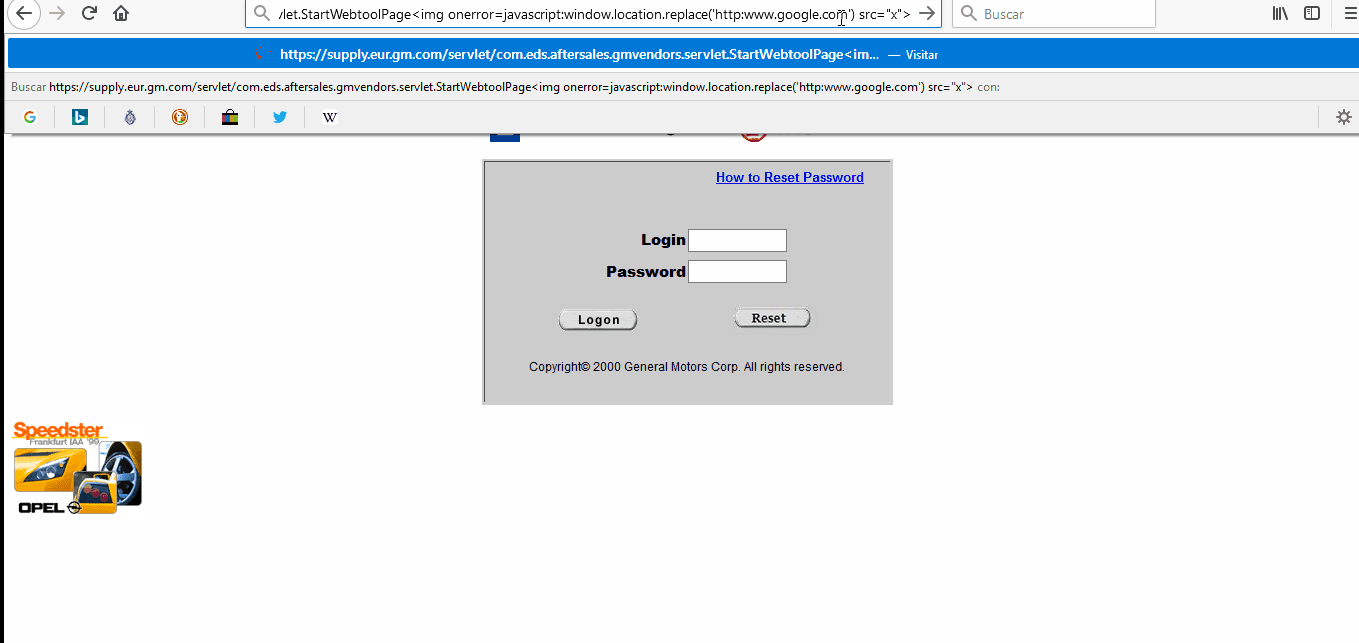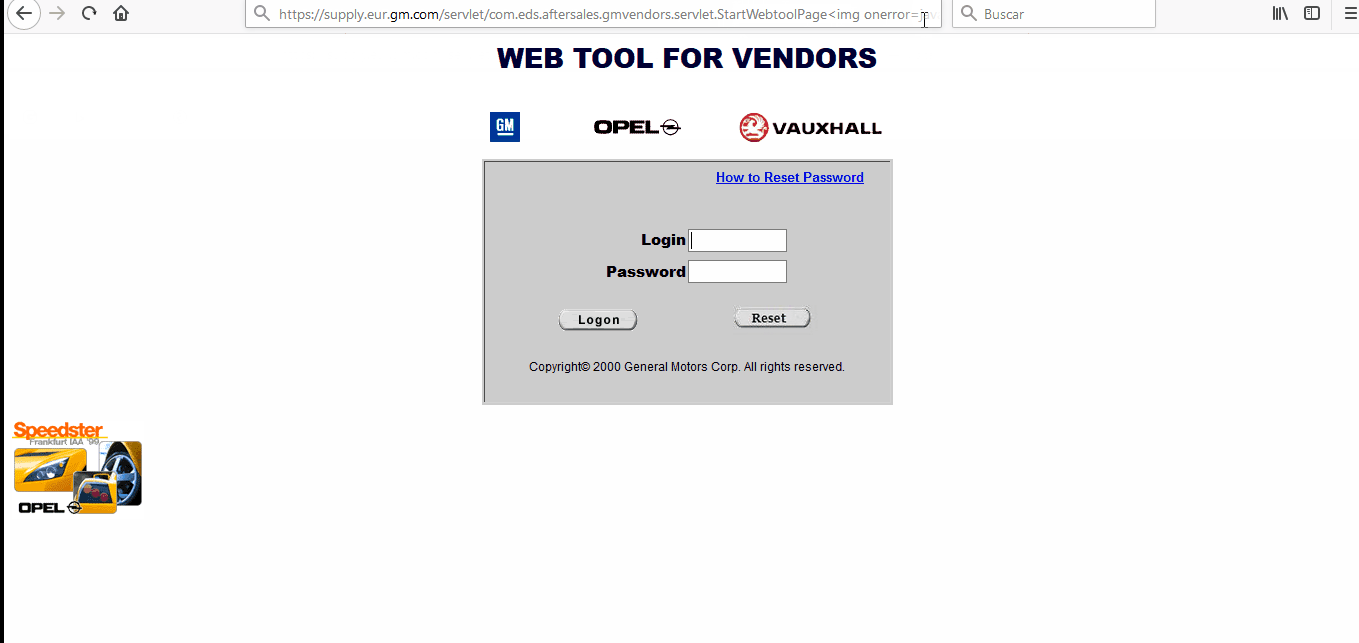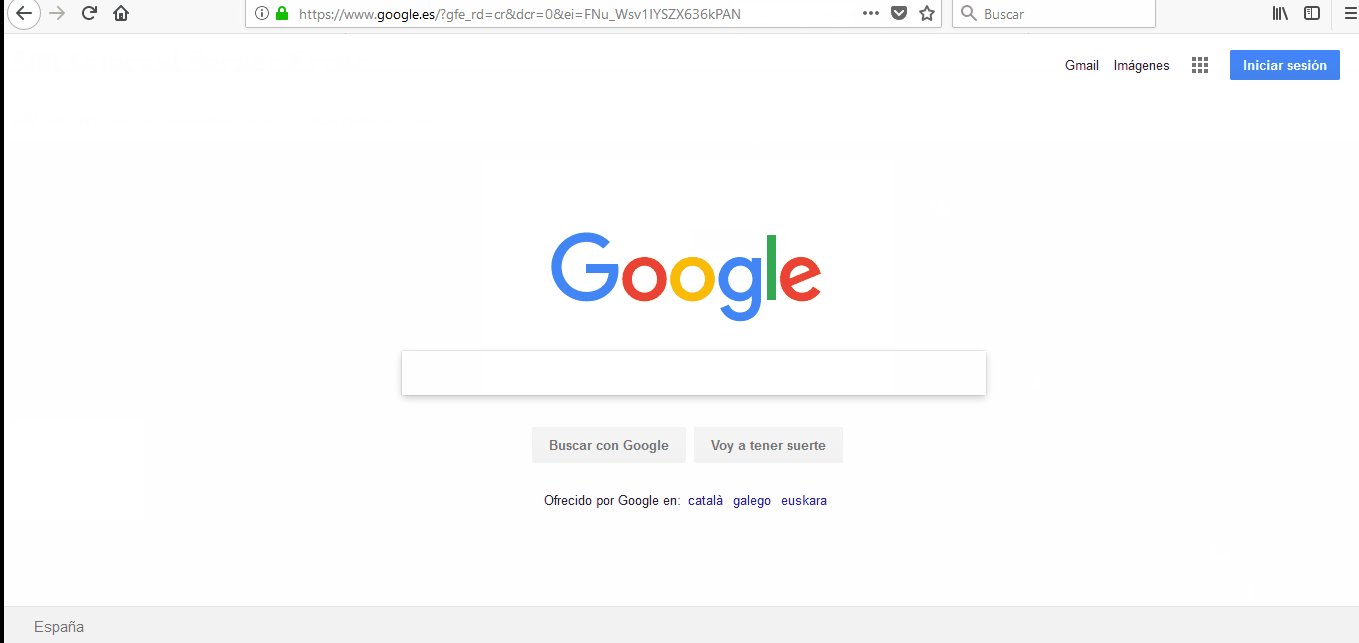
These XSS vulnerabilities type allow an attacker to, for example, redirect a legitimate sub-domain to a cloned website to achieve a phishing attack.
Unfortunately, the compensation for the work done by GM was zero, and this often happens.